Cryptography, also called cryptology, involves the use of code to secure information and communication.
The purpose of cryptography is to safely secure or pass sensitive information across various insecure platforms so that only the intended recipient can access the data and process it.
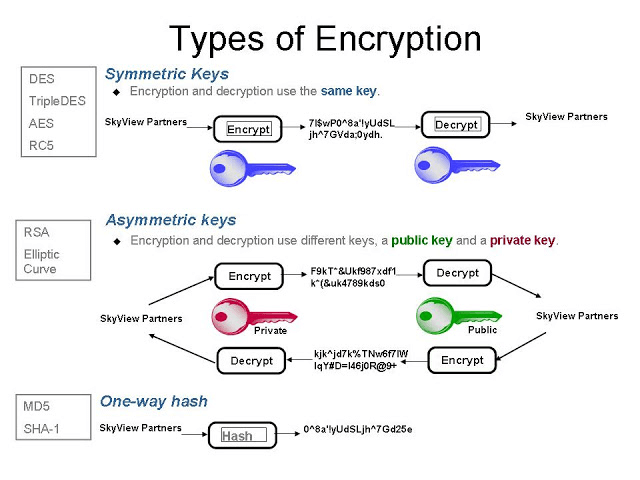
Generally, there are three different types of cryptography: symmetric key, hash functions, and asymmetric key. Each encryption method has its own uses, advantages, and disadvantages.
Hash functions, for example, are resistant to tampering, but are not as flexible in their use as the other methods.
Which Encryption Types Involve Keys?
Symmetric key and asymmetric key cryptography make use of keys for encryption and decryption.
The hash function doesn’t require the use of any key; instead, it takes an input of arbitrary length and provides the output in fixed length.
Hashing is almost always preferable to encryption when storing passwords inside databases because in the event of a data compromise, attackers will not have access to the plaintext passwords, and the website will not ever know the user’s plaintext password.
If you’ve ever received those notices that “our representatives will never ask for your password” from various companies, that’s part of the reason why they won’t: They have no use for it because they don’t have your password. They have a non-reversible cryptographic representation of your password—its hash value.
https://www.csoonline.com/article/3602698/hashing-explained-why-its-your-best-bet-to-protect-stored-passwords.html
Use Hash Functions for Passwords
Hashing is a one-way cryptographic function responsible for converting large inputs into small fixed outputs, which are stored in a hash table. Hashing is not reversible, while encryption is designed to work both ways.
Encryption algorithms take input and a secret key and generate a random-looking output called a ciphertext. This operation is reversible; anyone who obtains the secret key can decrypt the ciphertext and read the original input.
Uses Cases for Both Asymmetric and Symmetric Encryption
Encryption is not always either-or; there are many use cases in which both symmetric and asymmetric cryptography are called upon to improve both transaction speed and security. Since symmetric encryption is faster, often it is employed to encrypt the bulk of the information, and then asymmetric cryptography is used to encrypt the symmetric encryption/decryption key (then that key can be used to decrypt the full message contents).
Some of the most common uses for this hybrid approach include:
- Secure Messaging Apps: Signal App, for example, uses asymmetric cryptography to verify the identity of participants at the start of a conversation, and then symmetric cryptography to encrypt the ongoing contents of the conversation
- SSL/TLS: Uses asymmetric cryptography to encrypt a single-use symmetric encryption key, which is then used to encrypt/decrypt the contents of that internet browsing session
Symmetric vs. Asymmetric Key Encryption
To better understand how encryption works with asymmetric keys, it is necessary to begin by describing how encryption works with a symmetric key. In this symmetric key encryption, the key used by the party which sends and encrypts the message at one end, and the party who receives and decrypts it at the other end, is the same — hence the term symmetrical. The challenge for the parties is to exchange the common key in a secured manner.
Symmetric key cryptography involves the use of the same single common key by both the sender and the recipient for encryption and decryption purposes.
Better Security: Asymmetric Encryption
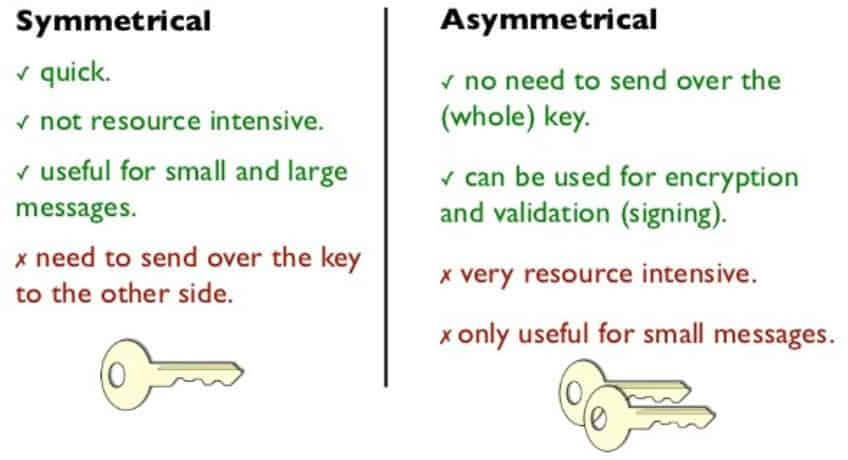
Both Asymmetric Key and Symmetric Key cryptography are effective for securing information and communication. However, Asymmetric offers better security because it utilizes two different, but mathematically related keys instead of one single key that must be securely sent and received. Asymmetric encryption is not suitable for long sessions because of the processing power it takes to calculate the complex math involved.
Faster Speed: Symmetric Encryption
Symmetric key is faster to encrypt, that’s why SSL uses symmetric keys for encrypting the traffic, and uses asymmetric keys to exchange the symmetric session key.
Asymmetric encryption is slower and mathematically complex but it solves the issue of key exchange. Symmetric encryption is faster but key exchange is a problem. So when a connection is established, key exchange is done using asymmetric encryption, and data transfer is done using symmetric encryption.
Elliptic Curve Cryptography
The Elliptic Curve Cryptography (ECC) encompasses a family of public-key cryptosystems. ECC implements all major capabilities of the asymmetric cryptosystems: Encryption, Signatures and Key Exchange.
The Elliptic Curve algorithm can be used for public/private key cryptography. The main advantage to ECC is that keys are a lot smaller. With RSA, for example, you need key servers to distribute public keys. With Elliptic Curves, you can provide your own public key.
ECC is a widely used standard mode of encryption. Various web applications depend upon its security, and ECC is expected to grow, owing to its shorter key length, strong security, and real-world effectiveness.
Uses of ECC
Elliptic curve cryptography encryption is one of the most generally used application techniques for digital signatures in various cryptocurrencies.
Elliptic curve cryptography is used to:
- Protect the sensitive data and internal interactions in the U.S. government,
- Maintain and assure anonymity in TOR project,
- Prove key ownership of Bitcoins,
- Provide signatures in Apple’s iMessage service,
- Encode DNS data with DNSCurve.
Bitcoin and Ethereum cryptocurrencies employ the Elliptic Curve Digital Signature Algorithm (ECDSA key). ECC is also the most favoured process for authentication over SSL/TLS for safe and secure web browsing.
ECC & Bitcoin
The encryption method of Elliptic Curve Cryptography is incorporated in the Bitcoin Protocol to generate a public key from the private key.
In practice, a private key is a number of 256 bits obtained in a random manner. It is also recommended to use a sophisticated pseudo-random system (a cryptographically secure pseudo-random number generator – “CSPRNG”) to generate your private key to ensure maximum security.
The private key is then used to generate the public key using a multiplication on an elliptic curve:
The private key (K) will be multiplied by a point generator (G) located on the curve and the result will correspond to the public key (K), another point on the curve (or K = K*g). Without entering into the details of the multiplication on elliptic curve, it is important to note that the point (k) can be obtained from (k) and (g), but it is impossible to obtain the point (k) from (K) and (g) and this, although (G) is constant for all generations of bitcoin key.
What is a Digital Signature?
- Digital signatures and SSL certificates secure websites
A digital signature is an asymmetric cryptosystem in which a sender uses a secret signature key to calculate a value for a digital message. Thus, using a private key, a sender can both decrypt a message after it was encrypted using the public key and sign a transaction message that allows the public to verify the authenticity of any non-encrypted message using their public key.
ECC is applied in digital signatures through Elliptic Curve DSA (ECDSA key) and in key exchange through Elliptic Curve Diffie-Hellman (ECDH). These algorithms are used in different parts of the SSL standard utilizing signing SSL certificates with ECDSA instead of RSA.
Key Generation and the Algorithms App
The generation of both the public and private keys depends on the algorithms of cryptography.
These algorithms are based on one-way functions — mathematical problems that are very easy to compute in one direction but pretty difficult to invert. Both “easy” and “difficult” used in the above context can be interpreted relative to some specific computing entity: easy enough for owners of the keys to access, and fairly difficult or very time and energy expensive for malicious agents to gain access.
Key Pair Generations Based on Prime Numbers
The cryptographic key pair is based on prime numbers of long length.
Both the public and private keys are computed together in the same mathematical process, using “trapdoor” functions. The hallmark trait of “trapdoor” functions is that they are easy to compute in one direction, yet difficult to compute in the opposite direction (difficult to calculate a private key from its mathematically related public key) without special information.
Note: Bitcoin Does Not Use Encryption Keys
The fact that the parties use the same key necessarily implies an element of trust between the transmitter and the receiver. In decentralized systems such as cryptocurrencies, the parties do not know each other, so symmetric keys are not used. Cryptocurrencies are connected in a decentralized peer-to-peer format; these systems are trustless because there is no central authority to orchestrate the transactions. The transactions that secure the blockchain are verified via consensus mechanisms.